Table of Contents
HCCAP format description
Note: all versions of oclHashcat have been replaced by a unified OpenCL CPU/GPU version, now known simply as hashcat.
Description
Note: The hccap file format has been replaced by hccapx.
HCCAP is a custom format, specifically developed for oclHashcat.
The data itself does not differ from usual tcpdump format. In fact, it's absolutely the same. It is just rearranged a bit.
A valid hashcat cap file (file extension: .hccap) contains one or more instances of the struct type documented below. If you have several single .hccap files which you want to merge into a single file (say multi.hccap), one can accomplish this by just concatenating one file(s) one to the other(s):
Attention: currently only oclHashcat supports loading and cracking of muliple networks at once. Multi-hccap support is currently not available in hashcat (CPU-based version).
Linux:
$ cat single_hccaps/*.hccap > all_in_one/multi.hccap
Windows:
copy /b single_hccaps\*.hccap all_in_one\multi.hccap
or select single ones
copy /b single_hccaps\1.hccap + single_hccaps\2.hccap all_in_one\multi.hccap
It seems that also cap2hccap is able to generate .hccaps that contain several networks (i.e. more than one struct instance, multiple networks w/ possibly different essid)
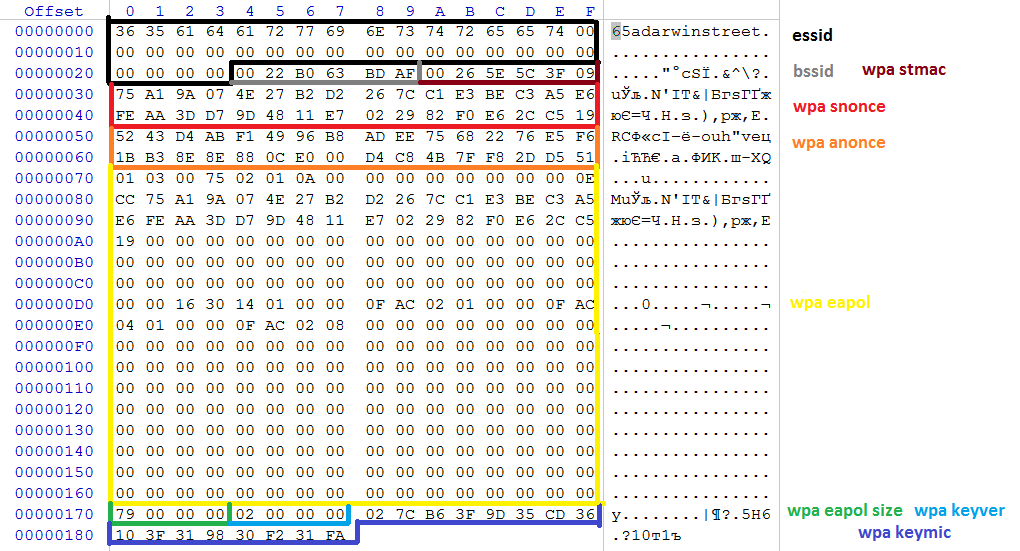
Screenshot
C Structure
typedef struct
{
char essid[36];
unsigned char mac1[6];
unsigned char mac2[6];
unsigned char nonce1[32];
unsigned char nonce2[32];
unsigned char eapol[256];
int eapol_size;
int keyver;
unsigned char keymic[16];
} hccap_t;
Detailed Structure
| Attribute name | Offset range | Attribute description |
|---|---|---|
| Essid | 0x00 to 0x23 | the essid(name) of the access point |
| Bssid | 0x24 to 0x29 | the bssid(MAC) of the access point |
| Wpa stmac | 0x2A to 0x2F | the MAC address of a client connecting to the access point |
| Wpa snonce | 0x30 to 0x4F | random salt used for handshake by both parties |
| Wpa anonce | 0x50 to 0x6F | random salt used for handshake by both parties |
| Wpa eapol | 0x70 to 0x16F | EAPOL |
| Wpa eapol size | 0x170 to 0x173 | size of eapol |
| Wpa keyver | 0x174 to 0x177 | the flag used to distinguish WPA from WPA2 ciphers. Value of 1 means WPA, other - WPA2 |
| Wpa keymic | 0x178 to 0x187 | the final hash value. MD5 for WPA and SHA-1 for WPA2 (truncated to 128 bit) |